[SOLVED] ELI5: How to put several servers on one external IP?
-
There's nothing saying you can't have ports forwarded for the NAS, and have a VPN for everything else. Censorship may be a problem, but those more often block VPN services like NordVPN, not protocols. So running your own is less likely to be stopped. That said, of course comply with local laws, I don't know where you live or what's legal there.
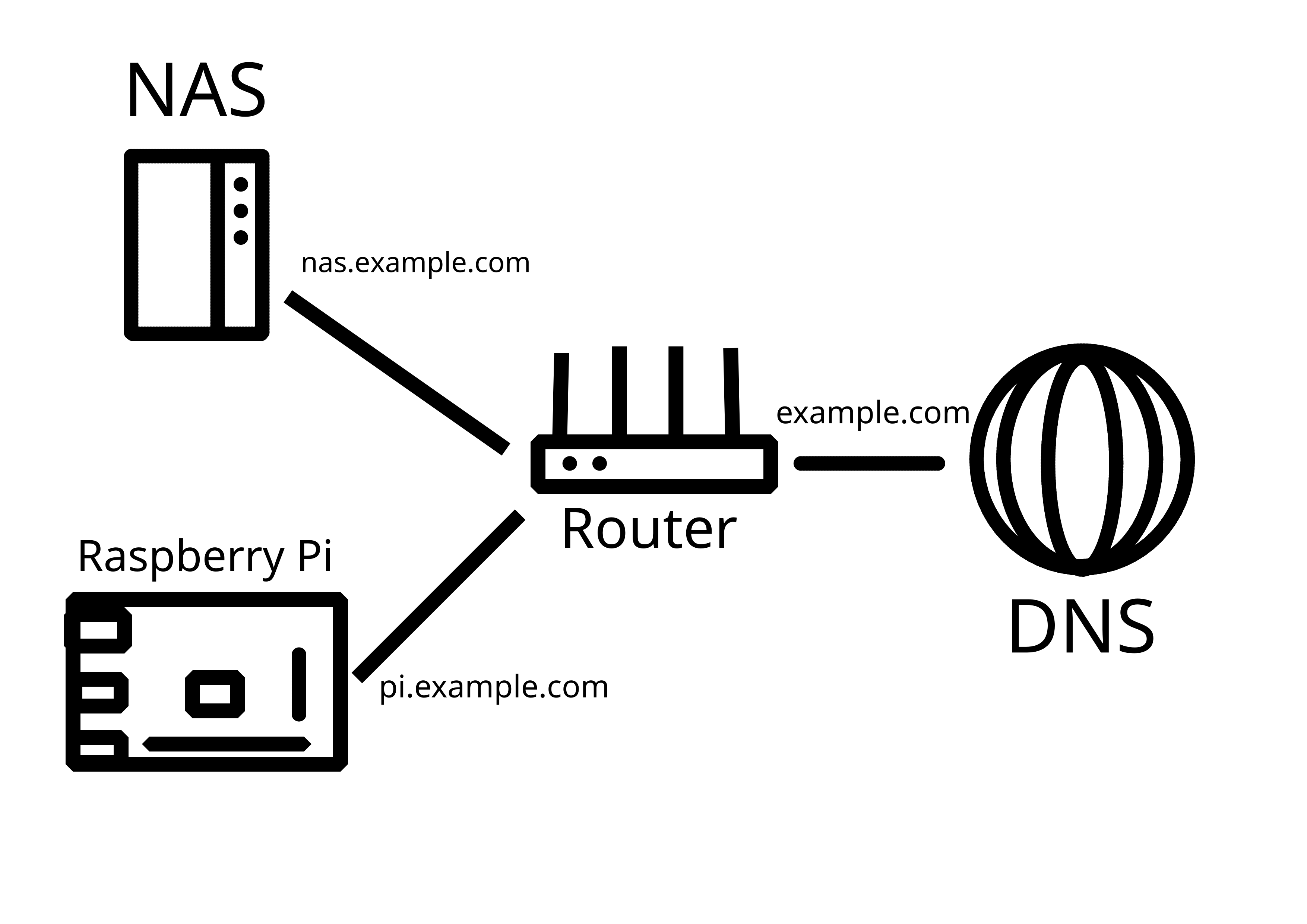
If you really want multiple things exposed at the same time, you have two options(which can be used in combination if needed/wanted):
- A reverse proxy. I use caddy. I give it a config file that says what address and port binds to what hostname, and I forward port 443/80 to it. That works great for web content.
- Use custom ports for everything. I saw someone else walking you through that. It works, but is a little harder to remember, so good notes will be important.
I still recommend against forwarding a lot of ports as a beginner. It's very common for software and web apps to have security vulnerabilities, and unless you are really on top of it, you could get hit. Not only does that put all your internal devices at risk, not just the one that was original breached, it also will likely become part of a botnet, so your local devices will be used to attack other people. I'd recommend getting confident with your ability to maintain your services and hardening your environment first.
It's not illegal to use VPN in my area, but connections are blocked on a protocol level, both through OpenVPN and Wireguard.
I already managed to make caddy work, so, hooray!
I also found a setting on my router that fully isolates certain devices from the local network. I want to put the server in there, so that the rest of my LAN is not under threat. I also want to figure out VLANs.
-
It's definitely not the same thing.
I do understand reservations behind usage free-tier services from Big Bad Corp., but I don't understand malicious reduction of valid arguments for usage of those services.It literally does the same thing, except it's self hosted?
-
Update: tried Caddy, love it, dead simple, super fast, and absolutely works!
Did you also forward UDP port 443?
If not I would as well since it is used for QUIC which is supported and automatically turned on for Caddy.
-
That's a good piece of advice, but due to several considerations (extreme censorship interrupting VPN connections, family using NAS for automatic backups, and some others) I cannot go that route.
wrote last edited by [email protected]What do you mean by blocked at a protocol level? You might give it a try on a random port to see what happens.
You could also look into port knocking. It is dated but still worth while.
-
It's not illegal to use VPN in my area, but connections are blocked on a protocol level, both through OpenVPN and Wireguard.
I already managed to make caddy work, so, hooray!
I also found a setting on my router that fully isolates certain devices from the local network. I want to put the server in there, so that the rest of my LAN is not under threat. I also want to figure out VLANs.
I am not an expert on security and I don't know how to setup ddns, but I simply use Tailscale VPN to access my RPi4 homeserver running Umbrel from outside of my home, I simply installed Tailscale in my Umbrel and in my phone, and when I want to access from my phone Immich, Nextcloud or any other app running on my Umbrel. I simply enable the Tailscale VPN. Maybe it has some limitations, but is the simpler way I found, and based on what I read, it is more secure than exposing a port in the router, but not sure.
-
What do you mean by blocked at a protocol level? You might give it a try on a random port to see what happens.
You could also look into port knocking. It is dated but still worth while.
wrote last edited by [email protected]I mean any connection through these protocols is just not working over the Internet. DPI equipment detects respective packets and cuts the connection, irrespective of the port you assign.
-
I am not an expert on security and I don't know how to setup ddns, but I simply use Tailscale VPN to access my RPi4 homeserver running Umbrel from outside of my home, I simply installed Tailscale in my Umbrel and in my phone, and when I want to access from my phone Immich, Nextcloud or any other app running on my Umbrel. I simply enable the Tailscale VPN. Maybe it has some limitations, but is the simpler way I found, and based on what I read, it is more secure than exposing a port in the router, but not sure.
I would be fairly comfortable running a direct WireGuard connection even without Tailscale, but my location and use case simply won't allow me to.
Your setup is valid, nothing wrong with it, and yes, it is more secure. Just can't be used in my case.
-
It literally does the same thing, except it's self hosted?
No public server required at all
-
CF: Yes
-
frp: No
DDoS protection, WAF, and automatic SSL
-
CF: Yes
-
frp: No
Access controls and auth
-
CF: built-in Zero Trust
-
frp: manual setup of token/OIDC
Managed DNS
-
CF: Yes
-
frp: No
Built in security tools
-
CF: Yes
-
frp: No
Just like I said - prevalent reduction of valid arguments for usage of those services.
-
-
Why wouldn't you setup a firewall on the VPS?
wrote last edited by [email protected]all home routers have NAT which functions as a firewall, but VPSes don't cone with any firewall by default, so you'd have to set one up. Also VPS ranges seem to hotter for scanning.
-
all home routers have NAT which functions as a firewall, but VPSes don't cone with any firewall by default, so you'd have to set one up. Also VPS ranges seem to hotter for scanning.
wrote last edited by [email protected]You don't need NAT for a Firewall. NAT doesn't provide any security benefits what so ever.
If you put something on the internet it should always have a Firewall. Use either ufw or firewalld. I don't see your argument since anything the bots can each will get probed.