[SOLVED] ELI5: How to put several servers on one external IP?
-
Drives are somewhat noisy (even though I took fairly quiet ones) and I appreciate total silence at night. Unfortunately, I don't have many places to put it outside my single room, so there's that.
I'd love to move to SSDs for storage at some point (I know it's controversial, but they would fit my use case better), but for now it's too expensive for me.
Ahh, that's valid. I've been wanting to build a (relatively) small 16TB SSD NAS for video editing, after which I could dump footage to my main NAS. SSD NAS systems can definitely make sense depending on your use case. Hell, you can even game off of them if you've got 10gig networking.
-
Ahh, that's valid. I've been wanting to build a (relatively) small 16TB SSD NAS for video editing, after which I could dump footage to my main NAS. SSD NAS systems can definitely make sense depending on your use case. Hell, you can even game off of them if you've got 10gig networking.
wrote last edited by [email protected]I'd love to eventually have a 10gbps LAN, yep

I'd also love to explore the technology going into cloud gaming, so not only would I launch games using files laying on the server, but could actually play them everywhere from my energy efficient potato laptop

But that's long ahead and more of an "if it even works properly"
-
Pretty solid!
Though insta-ban on everything :80/443 may backfire - too easy to just enter the domain name without subdomain by accident.Could be indeed. Looking at the nginx logs, setting a permaban on trying to access /git and a couple of others might catch 99% of bots too. And ssh port ban trigger (using knockd for example) is also pretty powerful yet safe.
-
Not sure why you're downvote, you're absolutely right. People scan for open ports all day long and will eventually find your shit and try to break in. In my work environment, I see thousands of login attempts daily on brand new accounts, just because something discovered they exist and want to check it out.
Those who have not been burned yet often don't expect it to happen to them. Usually it isn't anything big causing it but some typo in a config or software not updated on time.
-
In what way? It is a physical server located in my bedroom, sharing resources online.
Dude above you over is under the perception that it requires 100% uptime or other users to to be classified, which is wrong. You are definitely self hosting, albeit only for yourself I assume. Which is fine
-
Thanks! I got that advice as well, but I would like to keep it self-hosted - I consider using Pangolin on a VPS for that purpose going forward: https://github.com/fosrl/pangolin
Also, beware of the new attack on Cloudflare Tunnel:
https://www.csoonline.com/article/4009636/phishing-campaign-abuses-cloudflare-tunnels-to-sneak-malware-past-firewalls.htmlThis attack targets end users, not Cloudflare tunnel operators (i.e. self-hosters). It abuses Cloudflare Tunnels as a delivery mechanism for malware payloads, not as a method to compromise or attack people who are self-hosting their own services through Cloudflare Tunnels.
-
While not supportive of Big Tech, I do appreciate your piece of advice, and understand self-hosting needs differ!
P.S. Also beware, seems like there's a new attack through Tunnels:
Again, attack targets end users, not Cloudflare tunnel operators: It abuses Cloudflare Tunnels as a delivery mechanism for malware payloads, not as a method to compromise or attack people who are self-hosting their own services through Cloudflare Tunnels.
-
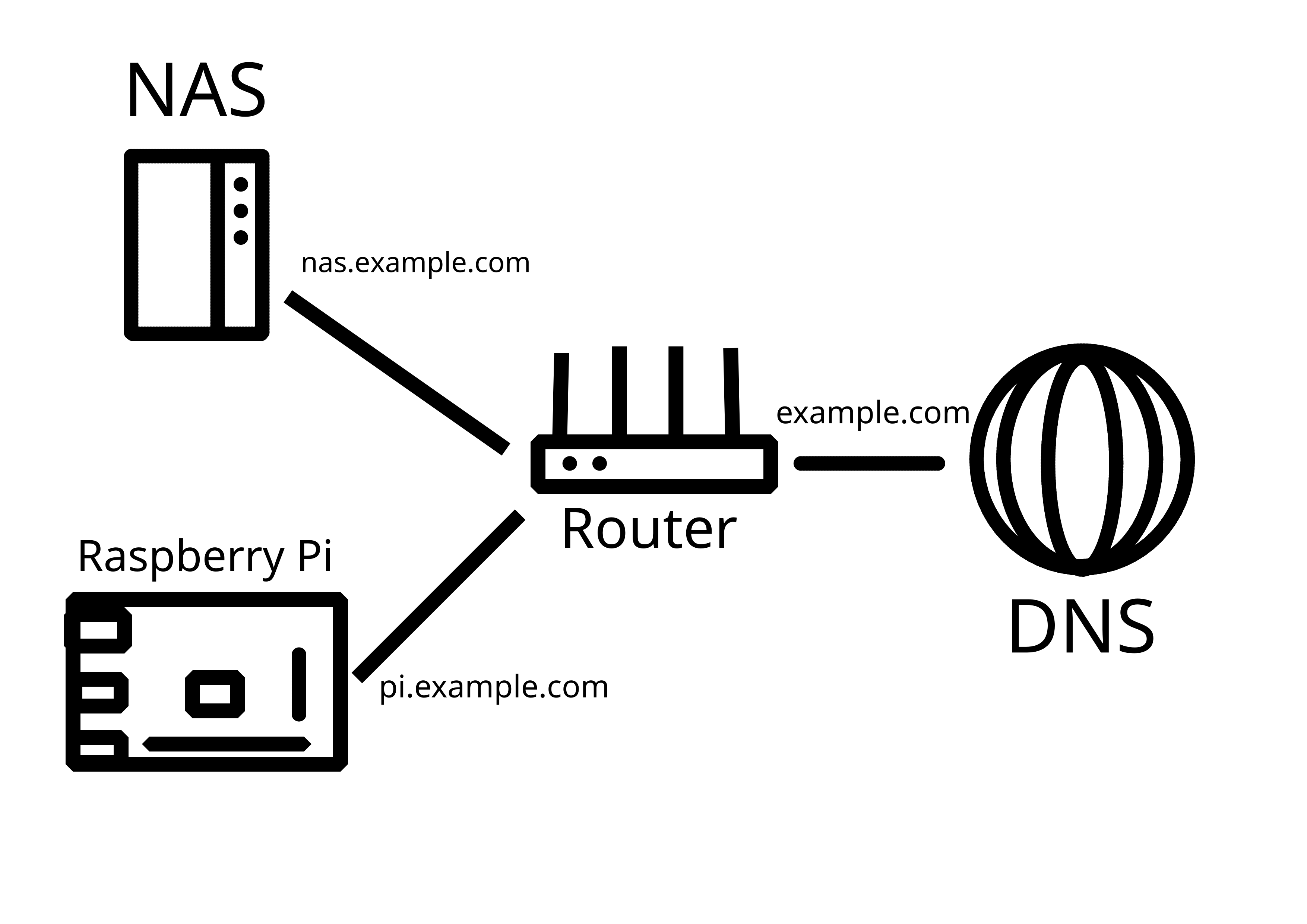
I'm pretty new to selfhosting and homelabs, and I would appreciate a simple-worded explanation here. Details are always welcome!
So, I have a home network with a dynamic external IP address. I already have my Synology NAS exposed to the Internet with DDNS - this was done using the interface, so didn't require much technical knowledge.
Now, I would like to add another server (currently testing with Raspberry Pi) in the same LAN that would also be externally reachable, either through a subdomain (preferable), or through specific ports. How do I go about it?
P.S. Apparently, what I've tried on the router does work, it's just that my NAS was sitting in the DMZ. Now it works!
What are you running?
If it is http based use a reverse proxy like Caddy
-
You can use frp to do the same thing a CloudFlare tunnel does without giving them your unencrypted data.
It's definitely not the same thing.
I do understand reservations behind usage free-tier services from Big Bad Corp., but I don't understand malicious reduction of valid arguments for usage of those services. -
NAT translation, i use my openwrt router for that
OpenWRT also has great IPv6 support
-
Your stuff is more likely to get scanned sitting in a VPS with no firewall than behind a firewall on a home network
Why wouldn't you setup a firewall on the VPS?
-
They are a plague with how prevalent they have become.
The internet shouldn’t put all its eggs into one basket.
It’s just another centralized entity which will lead to monopolized power. It goes against what we are trying to do with federated networks like Lemmy and mastodon.
wrote last edited by [email protected]I prefer to use products and services before inevitable enshittification, not after the curve. Refusing to use them won’t change their fate.
-
What are you running?
If it is http based use a reverse proxy like Caddy
For now just some experiments alongside NAS
Planning to host Bitwarden, Wallabag and other niceties on the server, and then when I get something more powerful, spin up Minecraft server and stuff
-
This attack targets end users, not Cloudflare tunnel operators (i.e. self-hosters). It abuses Cloudflare Tunnels as a delivery mechanism for malware payloads, not as a method to compromise or attack people who are self-hosting their own services through Cloudflare Tunnels.
Thanks for clarification!
-
Dude above you over is under the perception that it requires 100% uptime or other users to to be classified, which is wrong. You are definitely self hosting, albeit only for yourself I assume. Which is fine
Yep, sharing stuff for others requires more expertise, as I'll get responsible for other people's experience. If I screw something up now, only I will be affected.
-
Yep, sharing stuff for others requires more expertise, as I'll get responsible for other people's experience. If I screw something up now, only I will be affected.
And you are self-sufficient, or whatever the word is. But that's the key thing for me, not having to rely on others for my services

-
What are you running?
If it is http based use a reverse proxy like Caddy
Update: tried Caddy, love it, dead simple, super fast, and absolutely works!
-
I'm pretty new to selfhosting and homelabs, and I would appreciate a simple-worded explanation here. Details are always welcome!
So, I have a home network with a dynamic external IP address. I already have my Synology NAS exposed to the Internet with DDNS - this was done using the interface, so didn't require much technical knowledge.
Now, I would like to add another server (currently testing with Raspberry Pi) in the same LAN that would also be externally reachable, either through a subdomain (preferable), or through specific ports. How do I go about it?
P.S. Apparently, what I've tried on the router does work, it's just that my NAS was sitting in the DMZ. Now it works!
I really feel like people who are beginners shouldnt play with exposing their services. When you set up Caddy or some other reverse proxy and actually monitor it with something like fail2ban you can see that the crawlers etc are pretty fast to find your services. If any user has a very poor password (or is reusing a leaked one) then someone has pretty open access to their stuff and you wont even notice unless you’re logging stuff.
Of course you can set up 2FA etc but that’s pretty involved compared to a simple wg tunnel that lives on your router.
-
Dude above you over is under the perception that it requires 100% uptime or other users to to be classified, which is wrong. You are definitely self hosting, albeit only for yourself I assume. Which is fine
yes. i ment the uptime. to me hosted means i can reach it in a digital way any time even if it is just wake on lan. but if you guys say some device running 8hrs a day is hosting I am fine with that.
-
I really feel like people who are beginners shouldnt play with exposing their services. When you set up Caddy or some other reverse proxy and actually monitor it with something like fail2ban you can see that the crawlers etc are pretty fast to find your services. If any user has a very poor password (or is reusing a leaked one) then someone has pretty open access to their stuff and you wont even notice unless you’re logging stuff.
Of course you can set up 2FA etc but that’s pretty involved compared to a simple wg tunnel that lives on your router.
My mantra is "plan to be hacked". Whether this is a good backup strategy, a read-only VM, good monitoring or serious firewall rules.