[SOLVED] ELI5: How to put several servers on one external IP?
-
Remember that with services facing public internet it's not about if you get hacked but when you get hacked. It's personal photos on someone elses hands then.
I do remember that and take quite a few precautions. Also, nothing that can be serioisly used against me is in there.
-
I will eventually!
But for all I understand, it is to put many services on one machine, and I already have a NAS that is not going anywhere
I've gone the other way. I used to run a Proxmox cluster, then someone gave me a Synology NAS. Now it's rare that I spin up Proxmox and instead use a mix of VMs, containers and Synology/Synocommunity apps.
-
Thanks! Syno one didn't work properly, but I got it to work through different means
Check it again, I used it for years before switching to something with more features
-
I've gone the other way. I used to run a Proxmox cluster, then someone gave me a Synology NAS. Now it's rare that I spin up Proxmox and instead use a mix of VMs, containers and Synology/Synocommunity apps.
Interesting!
But I don't want to mix it too much. I do have a Docker on it with just some essentials, but overall I'd like to keep NAS a storage unit and give the rest to a different server.
I treat NAS as an essential service and the other server as a place to play around without pressure to screw anything
-
Check it again, I used it for years before switching to something with more features
Will try!
-
Oh, nice! So I don't have just one, but many external IPs, one for every local device?
Yes, even IPv4 was intended to give each device in the world their own IP, but the address space is too limited. IPv6 fixes that.
Actually, each device usually has multiple IPv6s, and only some/one are globally routable, i.e. it works outside of your home network. Finding out which one is global is a bit annoying sometimes, but it can be done.Usually routers still block incoming traffic for security reasons, so you still have to open ports in your router.
-
Yes, even IPv4 was intended to give each device in the world their own IP, but the address space is too limited. IPv6 fixes that.
Actually, each device usually has multiple IPv6s, and only some/one are globally routable, i.e. it works outside of your home network. Finding out which one is global is a bit annoying sometimes, but it can be done.Usually routers still block incoming traffic for security reasons, so you still have to open ports in your router.
Nice to know!
-
I do remember that and take quite a few precautions. Also, nothing that can be serioisly used against me is in there.
I have wrestled with the same thing as you and I think nginx reverse proxy and subdomains are reasonably good solution:
- nothing answers from www.mydomain.com or mydomain.com or ip:port.
- I have subdomains like service.mydomain.com and letsencrypt gives them certs.
- some services even use a dir, so only service.mydomain.com/something will get you there but nothing else.
- keep the services updated and using good passwords & non-default usernames.
- Planned: instant IP ban to anything that touches port 80/443 without using proper subdomain (whitelisting letsencrypt ofc), same with ssh port and other commonly scanner ones. Using fail2ban reading nginx logs for example.
- Planned: geofencing some ip ranges, auto-updating from public botnet lists.
- Planned: wildcard TLS cert (*.mydomain.com) so that the subdomains are not listed anywhere maybe even Cloudflare tunnel with this.
Only fault I’ve discovered are some public ledgers of TLS certs, where the certs given by letsencrypt spill out those semi-secret subdomains to the world. I seem to get very little to no bots knocking my services though so maybe those are not being scraped that much.
-
I have wrestled with the same thing as you and I think nginx reverse proxy and subdomains are reasonably good solution:
- nothing answers from www.mydomain.com or mydomain.com or ip:port.
- I have subdomains like service.mydomain.com and letsencrypt gives them certs.
- some services even use a dir, so only service.mydomain.com/something will get you there but nothing else.
- keep the services updated and using good passwords & non-default usernames.
- Planned: instant IP ban to anything that touches port 80/443 without using proper subdomain (whitelisting letsencrypt ofc), same with ssh port and other commonly scanner ones. Using fail2ban reading nginx logs for example.
- Planned: geofencing some ip ranges, auto-updating from public botnet lists.
- Planned: wildcard TLS cert (*.mydomain.com) so that the subdomains are not listed anywhere maybe even Cloudflare tunnel with this.
Only fault I’ve discovered are some public ledgers of TLS certs, where the certs given by letsencrypt spill out those semi-secret subdomains to the world. I seem to get very little to no bots knocking my services though so maybe those are not being scraped that much.
Pretty solid!
Though insta-ban on everything :80/443 may backfire - too easy to just enter the domain name without subdomain by accident. -
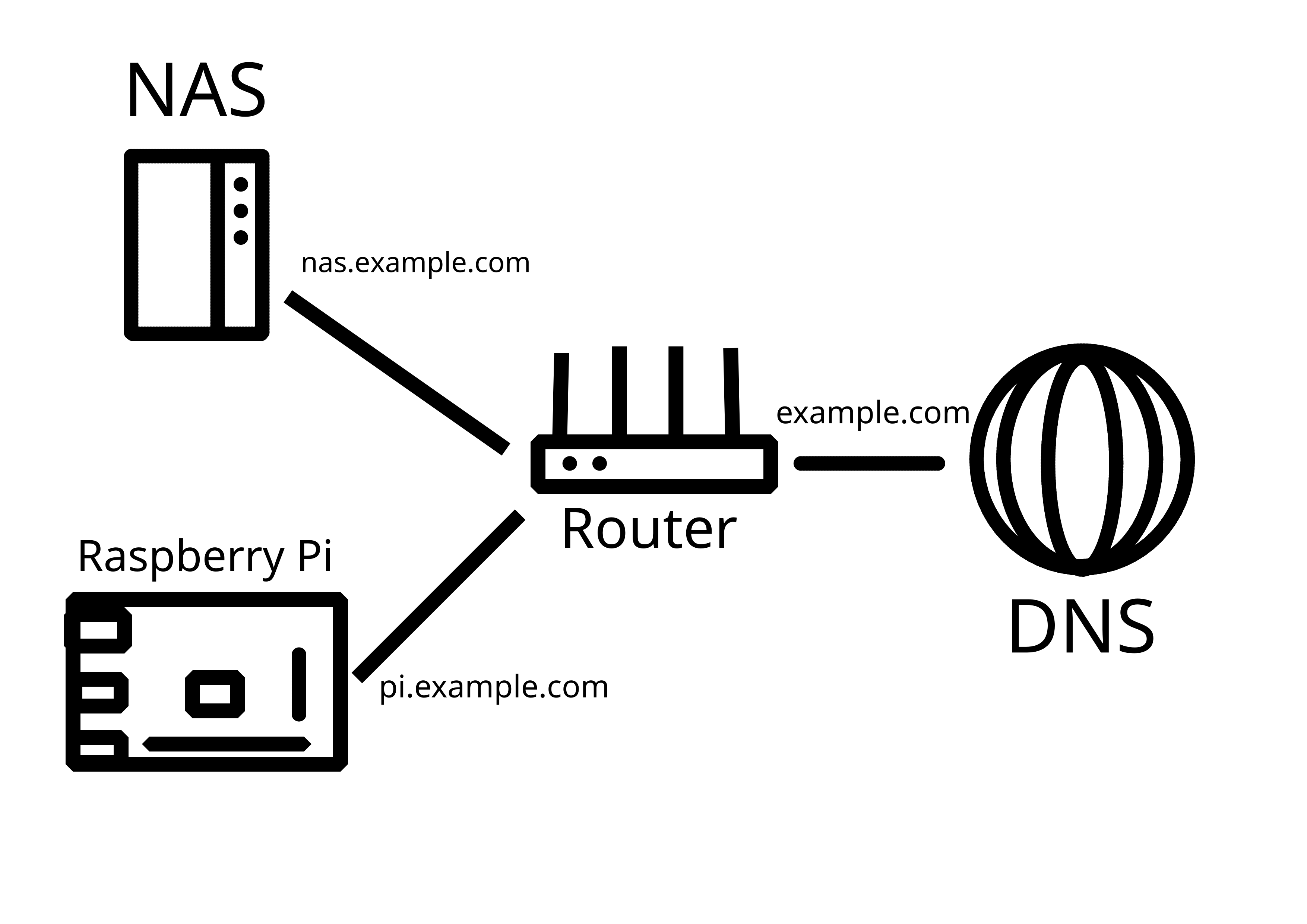
Where do I type rpi's IP, just in port forwarding? Or somewhere else?
I want for Nginx proxy, controlled through the Manager, to direct traffic to different physical servers based on subdomain.
I put in nas.my.domain and I get my Synology on its DSM port. I put in pi.my.domain and I get a service on my Pi.
It seems you are missing some very basic knowledge, if you have questions like this. Watch/read some tutorials to get the basics, than ask specific questions.
This guy does the same thing as you: https://www.youtube.com/watch?v=yLduQiQXorc
This was like the 3rd result for searching for nginxproxymanager on yt.
-
Your stuff is more likely to get scanned sitting in a VPS with no firewall than behind a firewall on a home network
Unless your home internet is CG-NAT, both have a publicly accessible IP address, so both will be scanned
-
It seems you are missing some very basic knowledge, if you have questions like this. Watch/read some tutorials to get the basics, than ask specific questions.
This guy does the same thing as you: https://www.youtube.com/watch?v=yLduQiQXorc
This was like the 3rd result for searching for nginxproxymanager on yt.
wrote last edited by [email protected]Guess I am going ahead of myself, yes, which gets even more complicated by having another server (Synology NAS) already installed and messing with networking a little, as internal settings appear to expect the NAS to be the only exposed thing on the network.
Thanks for the link! I've seen that thumbnail, but most guides are solely focused on actually installing Nginx Proxy Manager, which is the easy part, and skip the rest, so I glanced that one over.
P.S. Looks like I did everything right, I just need to sort my SSL stuff to work properly.
-
I'm pretty new to selfhosting and homelabs, and I would appreciate a simple-worded explanation here. Details are always welcome!
So, I have a home network with a dynamic external IP address. I already have my Synology NAS exposed to the Internet with DDNS - this was done using the interface, so didn't require much technical knowledge.
Now, I would like to add another server (currently testing with Raspberry Pi) in the same LAN that would also be externally reachable, either through a subdomain (preferable), or through specific ports. How do I go about it?
P.S. Apparently, what I've tried on the router does work, it's just that my NAS was sitting in the DMZ. Now it works!
The synology NAS can act as a reverse proxy for stuff inside your network. I don't have mine in front of me, so you will have to google the steps, but basically you point the synology to an internal resource and tell it what external subdomain it should respond to.
-
I'm pretty new to selfhosting and homelabs, and I would appreciate a simple-worded explanation here. Details are always welcome!
So, I have a home network with a dynamic external IP address. I already have my Synology NAS exposed to the Internet with DDNS - this was done using the interface, so didn't require much technical knowledge.
Now, I would like to add another server (currently testing with Raspberry Pi) in the same LAN that would also be externally reachable, either through a subdomain (preferable), or through specific ports. How do I go about it?
P.S. Apparently, what I've tried on the router does work, it's just that my NAS was sitting in the DMZ. Now it works!
wrote last edited by [email protected]Good to hear you figured it out with router settings. I'm also new to this but got all that figured out this week. As other commenters say I went with a reverse proxy and configured it. I choose caddy over nginx for easy of install and config. I documented just about every step of the process. I'm a little scared to share my website on public fourms just yet but PM me ill send you a link if you want to see my infrastructure page where I share the steps and config files.
-
The synology NAS can act as a reverse proxy for stuff inside your network. I don't have mine in front of me, so you will have to google the steps, but basically you point the synology to an internal resource and tell it what external subdomain it should respond to.
Yes, I know where this feature is in the settings, but it's got its own issues and I also turn the NAS off for the night, so it's not an option for me.
-
Good to hear you figured it out with router settings. I'm also new to this but got all that figured out this week. As other commenters say I went with a reverse proxy and configured it. I choose caddy over nginx for easy of install and config. I documented just about every step of the process. I'm a little scared to share my website on public fourms just yet but PM me ill send you a link if you want to see my infrastructure page where I share the steps and config files.
Thanks, I will! Wise of you not to share it publicly for security reasons
-
I'm pretty new to selfhosting and homelabs, and I would appreciate a simple-worded explanation here. Details are always welcome!
So, I have a home network with a dynamic external IP address. I already have my Synology NAS exposed to the Internet with DDNS - this was done using the interface, so didn't require much technical knowledge.
Now, I would like to add another server (currently testing with Raspberry Pi) in the same LAN that would also be externally reachable, either through a subdomain (preferable), or through specific ports. How do I go about it?
P.S. Apparently, what I've tried on the router does work, it's just that my NAS was sitting in the DMZ. Now it works!
You already have a lot of good answers ... but I got one more to add.
I have a very similar setup on my homelab and I'm using a Cloudflare tunnel.
It's a free service and it's really good because it allows you to expose web services and specific ports for remote access over dynamic IPs without having to expose your own router.
https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/
-
You already have a lot of good answers ... but I got one more to add.
I have a very similar setup on my homelab and I'm using a Cloudflare tunnel.
It's a free service and it's really good because it allows you to expose web services and specific ports for remote access over dynamic IPs without having to expose your own router.
https://developers.cloudflare.com/cloudflare-one/connections/connect-networks/
wrote last edited by [email protected]Thanks! I got that advice as well, but I would like to keep it self-hosted - I consider using Pangolin on a VPS for that purpose going forward: https://github.com/fosrl/pangolin
Also, beware of the new attack on Cloudflare Tunnel:
https://www.csoonline.com/article/4009636/phishing-campaign-abuses-cloudflare-tunnels-to-sneak-malware-past-firewalls.html -
Yes, I know where this feature is in the settings, but it's got its own issues and I also turn the NAS off for the night, so it's not an option for me.
Why do you turn off the NAS at night? Reminds me of my grandparents turning off the wifi at night.
-
Yes, I know where this feature is in the settings, but it's got its own issues and I also turn the NAS off for the night, so it's not an option for me.
then its not selfhosting.